We all have that one friend who keeps app-locks for all his applications instead of encrypting his device. It's like writing the password of your computer on sticky note and pasting it on your monitor. People forget that app-locks are application which you install on your phone. And if we just kill the process then the application will no longer protect your secrets.I tested 2 of the top play store app-locks, I don't indent to harm the reputation of the poor developers. But I would like to convey to them in simple words that "Your application is SHIT!".
How to?
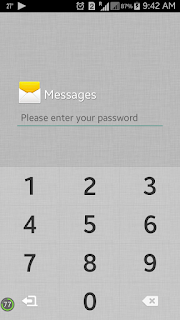
- Try opening a app which is protected by the app-lock, it will ask you some stupid PIN which I assume that you won't be knowing.
- Go to device settings & open Application Manager.
- Now locate the app-lock in the list and select it.
- Now click on force stop and open the the app which was locked initially, it will open.

- If the first trick doesn't work then go to the app-lock and select clear data. All the apps will be unlocked.
Note:-
Clearing the data will disable the app-lock permanently while force stopping will temporarily disable it.
Encrypting your entire device is the best protection. Another way is to lock the application manager with the app-lock.
Clearing the data will disable the app-lock permanently while force stopping will temporarily disable it.
Encrypting your entire device is the best protection. Another way is to lock the application manager with the app-lock.